
A worrying new development has surfaced in the Android world where phones are coming preinstalled with malware. often disguised as legitimate harmless apps these malicious apps post a security risk for users. The malware that is being found on these phones can gather sensitive user information, display annoying advertisements and compromise the security of the device. This new discovery shows how important it is to be cautious when downloading applications as well highlighting the need to have robust security measures in place, and carrying out updates at regular intervals using reputable application sources.
Google’s Play Store is notorious for allowing apps that have malware, adware or a flavour of spyware or fleeceware, onto the store. A less known fact is that hackers are increasing the use of preinstalled apps for their malicious activities. This is where threat researchers are trying to raise awareness about such a growing trend. The issue is that millions of affordable android phones come with certain apps pre installed on the device. The only thing a hacker needs to do is compromise one of those apps. For google this is a trickier issue to address in regards to such rogue apps finding their way into google Play Store.
With three billion world wide users, Android has taken another hit when malware was discovered in 60 Apps on the Play Store each having over 100 million downloads. What makes this even more concerning is that threat actors that develop these apps take advantage of various loopholes they are aware of in the application getting process. These malicious apps expunge around $400 million USD per user from their users by having them sign up for expensive in app subscriptions.
Trend Micro have been sounding this alarm about the growing number of android devices that come with such malicious apps pre installed. The sad truth is if there is an app that you have installed from the Google Play store that is malicious it is easy to remove just by uninstalling that particular application. On the other hand it is much more difficult if the malware is embedded in system applications or the firmware of the device.
the open source nature of Android allows phone manufacturers to create a wide range of models that provide price aware consumers with more affordable phone options. This in turn opens another door, this time for hackers where they can sneak malicious code in before the device even leaves the manufacturing floor. This issue is not limited to Android phones, also smartwatches, tables and set top boxes.
Fydor Yarochkin, Senior researcher at Trend Micro, says that malware coming preinstalled on devices has become rather common place in recent years. This is due to the rush to the bottom amongst mobile developers. When selling firmware became unprofitable so many developers began to offer it for free. With this change there is also a catch with this new way of operating.
Trend Micro analysed numerous firmware images and all these images contained “silent plugins.” 80 different types have been discovered so far, but only a handful have seen distribution on a wide spread scale. The most popular ones are sold on the underground black market as well as promoted on Facebook, YouTube and various blogs.
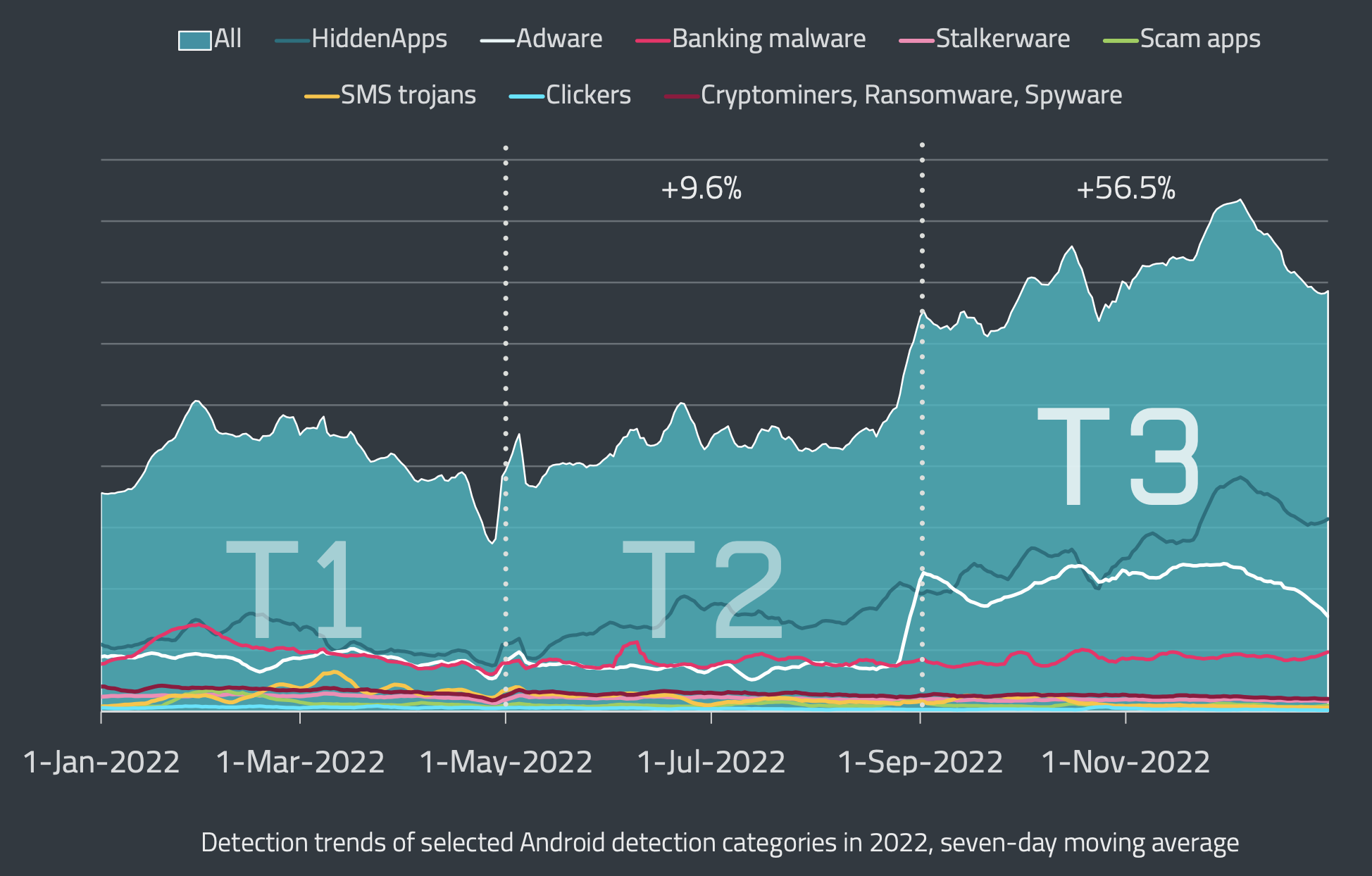
Data: ESET Threat Intelligence
The scary part with these plugins as it allows cyber criminals to rent ones compromised Android device for 5 minutes at a time. This allows criminals to steal sensitive user information and credentials. Other plugins can download additional malware onto an already compromised device.
Researchers believe that millions of Android infected devices are currently in use. The largest concentrated portion of these compromised devices can be found in Easter Europe, and Southeast Asia. What is an interesting thing to note is that the cyber criminals claim that there are almost 9 million such devices that have such silent plugins loaded.
It has been confirmed by Trend Micro that malware tends to be found on devices from at least 10 vendors, mainly Chinese vendors. It is also suspected by Trend Micro that 40 more vendors are affected. What Trend Micro is more interested in is understanding at what point in the supply chain these infections are most likely to occur.
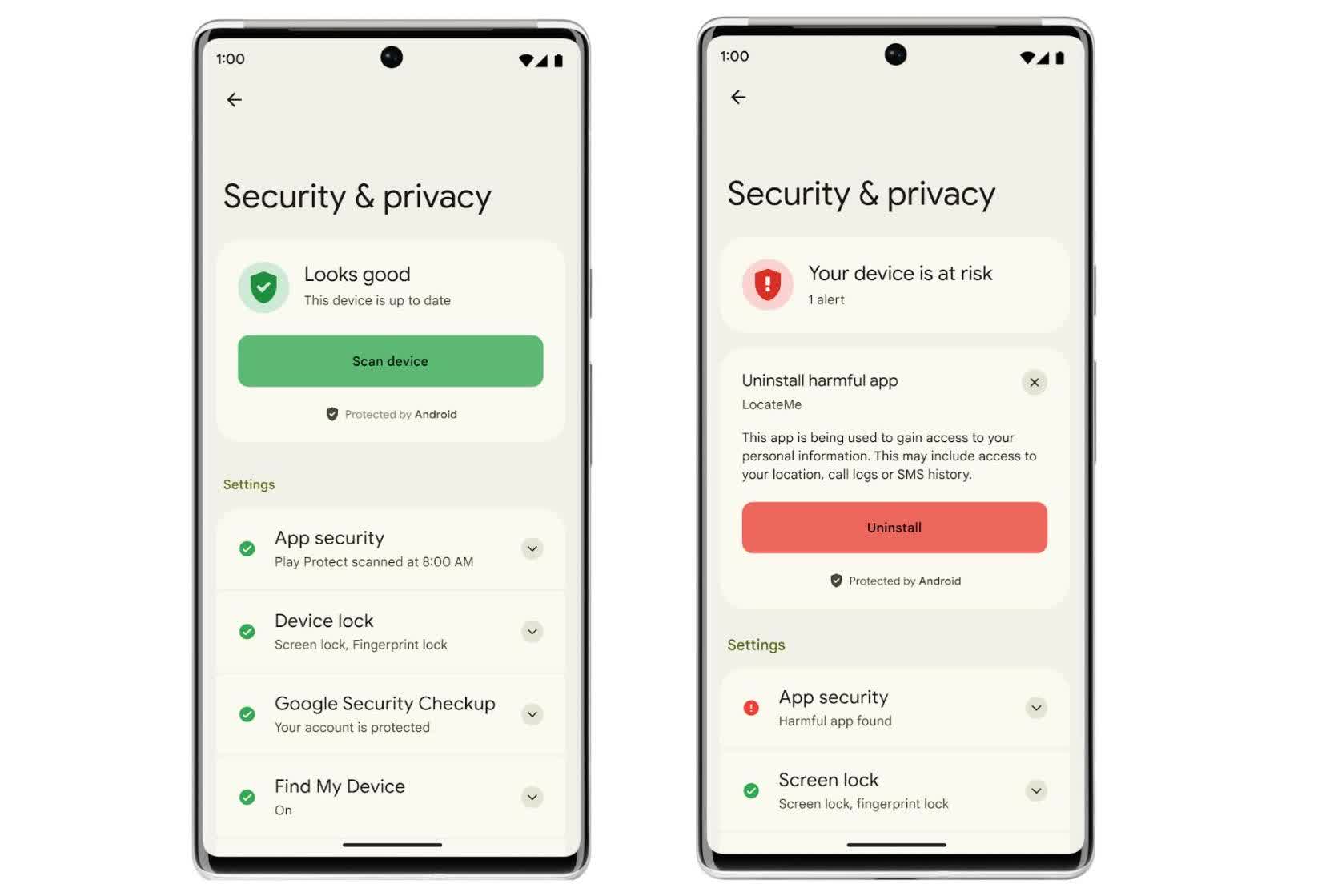
Usually Google’s Play Protect can find rogue apps, but only from the play store. What about those rogue apps that come as part of the device firmware?
This issue of preinstalled malware has been something Google has know for years, but its an issue that is not easy for them to solve due to limited control over the complex OEM Android supply chain. Lower cost phones go for the Android Open Source Platform (AOSP) and those come with around 100 to 400 apps preinstalled including ones that are malicious.
Around 225 device manufacturers tend to leave diagnostics software on the phones, which doesn’t help as these enable backdoor remote access for spyware and censorship tools. Numerous Chinese brands have been observed to have malware auto installers in the system updater. Some of these brands include Oppo, OnePlus, Realme, Xiaomi and Gigaset, which sells phones in the EU.
In 2019 Maddie Stone, a Google Project Zero research, revealed an SMS and ad fraud botnet called Chamois which has had an affect on at least 21 million Android devices in past years due to it coming as pre installed malware. It was discovered that vendors would unknowingly incorporate the code of this botnet into their android distributions because they were easily tricked into believing it was a legitimate ad service.
Google has since invested heavily in improving and refining Google Play Protect, extending its capabilities to monitor pre installed applications for malicious behaviour. With this said, hackers keep finding ways to bypass such protections. A business model has developed on the dark web making this a lucrative business. An analysis at Kaspersky found that accessing any malicious services can cost anywhere from $2,000 to $20,000 USD.
In order to protect yourself, Yarochkin, from Trend Micro, recommends going for higher end devices and using brands like Samsung and Google which report to have better supply chain security measures in place. It is important to also note that most antivirus apps for mobile are ineffective against real security threats. It is best not to rely on them unless you want to end up like thousands of individuals who downloaded password stealing malware which was disguised as an antivirus tool.
References:
https://www.techspot.com/news/98667-millions-android-phones-come-pre-installed-malware-there.html
Leave a Reply