
This post is a continuation of the other post, Malicious One Note Files are Being Used in Attempts to Gain Initial Access to Victim’s Networks, which shows how a malicious attack can happen with specially crafted one note files. This article will provide some guidance on how to mitigate OneNote attacks as well as what to look out for in terms of Indicators of Compromise (IoC).
Mitigations
The mitigations for this issue are very simple.
Usually if someone needs to share a OneNote file with you this is done through the share mechanisms of One drive. If you get OneNote files (with the .one extension) these are most likely malicious and should be blocked.
If blocking is not an option and these files must be allowed and accessed, it is important that the source is validated and credible.
Yara Rules were also created by Neo23x0 for detecting any suspiciously embedded file types in OneNote files.

Indicators of Compromise (IoC)
SHA256 Signature: DE9FDC6426C7DDF204FF5683130B7EAC03859F32D8F6860D99F849D759A3B84D
File Name: notes.one
File Type: OneNote file format
Details: Initial Payload
SHA256 Signature: d8202493557e94abeaeabd10f5940798e34fd73112a4a49468309e4c94195af9
File Name: putty.jpg
File Type: DLL
File Size: 448055 bytes
Details: Final payload executed with “rundll32.exe C:\programdata\putty.jpg,Wind”
SHA256 Signature: 8b02c7e9f0d7b08bf3dfc4feaa18363c9917e4ab35fda58c5720b723a9443b73
File Name: 1.png
File Type: DLL
File Size: 1780063 bytes
Details: Final payload executed with “rundll32.exe C:\ProgramData\1.png,Wind”
SHA256 Signature: 2544adb4a05f340fa280d596ca483ccc6d79b261233e40bb5b08855d4dc5b305
File Name: system32.bat
File Type: Win32 EXE
File Size: 35328 bytes
Details: Final payload executed with “Start-Process -Filepath $env:tmp\system32.bat62576”
SHA256 Signature: 8C3DD90C78A217A15530E3CD96AE28E0DB7B73A5734E709BEEE9509A2342A832
File Name: ComplaintCopy_25628(Feb01).one
File Type: OneNote file format
Details: Initial payload
There were other files that were observed but could not be gathered due to the AV destroying them.
Initial Payload OneNote Files
- AgreementCancelation_367226(Feb08).one
- Cancellation.one
- document.one
- DocumentsFolder_780693(Feb03).one
- Cancelation.one
- cancelation.one
- Secured-Document.one
- ComplaintCopy_75601(Feb01).one
Embedded OneNote attachments
- Open.cmd (Batch Script)
- as2ECOj.cmd (Batch Script)
- Open.hta (HTML Application Script)
- document.hta (HTML Application Script)
Final Payload files
- aYmyWrBC.jpg
- DLL executed with “rundll32.exe C:\programdata\aYmyWrBC.jpg,Wind”
- atzTG39.png
- DLL executed with “rundll32.exe C:\ProgramData\atzTG39.png,Wind”
- aCfzEaqD.png
- Deleted prior to execution
- index1.png
- DLL executed with “rundll32.exe C:\ProgramData\index1.png,Wind”
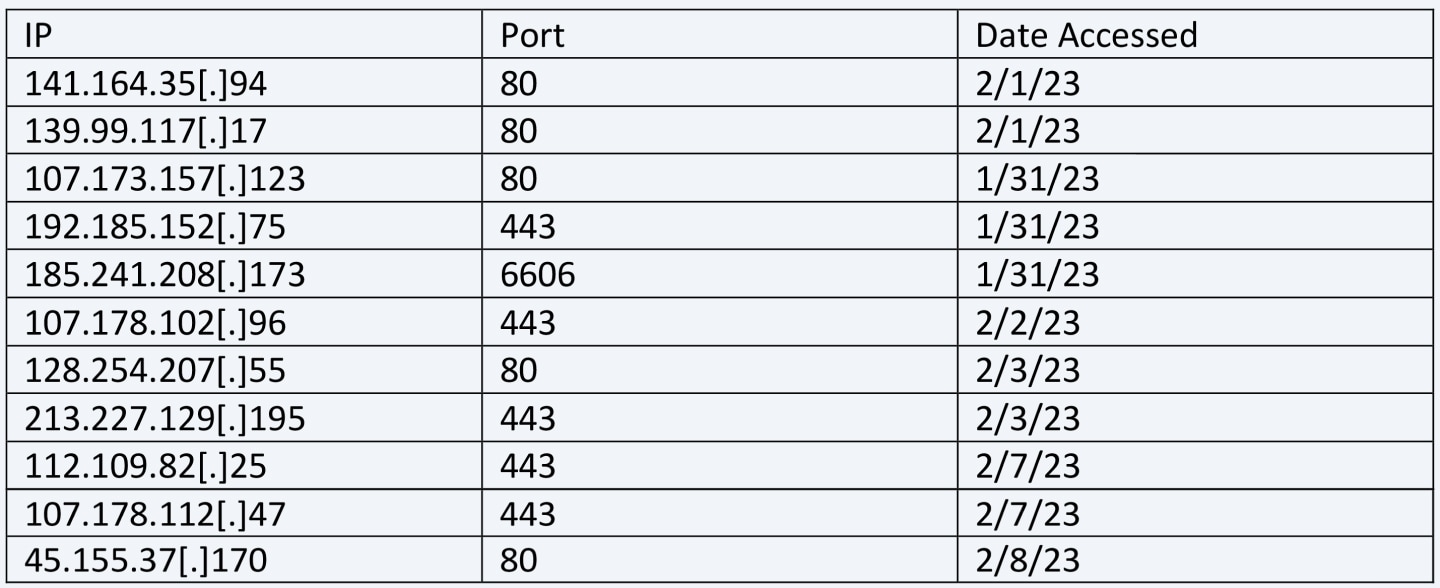
IP Addresses
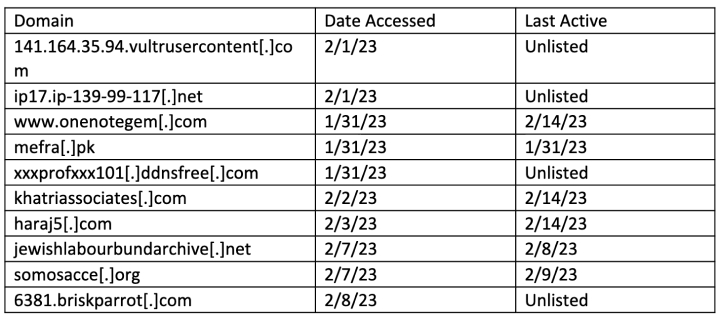
Domains

Reach out to us on sales@eagleeyet.net for a consultation on how we can potentially improve your security posture.
Reference:
https://blackpointcyber.com/resources/blog/with-one-foot-in-the-door/
Leave a Reply