
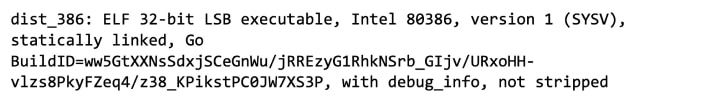
As of Februrary 2023, numerous instances of malicious Microsoft OneNote files (.one) have been detected and stopped from being used to obtain intial access to victims by BlackpointCyber’s SOC with similar techniques being used by various threat actors.
Macros have long been exploited as an initial access vector. in an April 2022 feature change, Microsoft blocks macros by default on any Office files which are downloaded from the internet. This means threat actors would need to adapt their tactics.
In this type of attack, a malicious file is sent as an attachment as part of a phishing email. This in turn requires the victim to open it and execute the payload. The types of payloads observed in such attacks contain scripts that in turn download and execute additional payload from the threat actors server. This in turn provides the threat actors with flexibility to launch various types of attacks as well as change the payloads as required.
Technical Deconstruction of This Type of Attack
The below screenshot is an example of what a malicious one note file shows when you open it with OneNote.
As a default, this application opens the file in read only mode and explains to the victim that there are additional attachments in the cloud.
Once edit mode is enabled the file in turn displays an “Open button”. This so called button is just a text box which is an overlay to an embedded batch file called “Open.cmd” which can be seen in the next screenshot
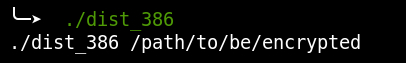
OneNote, which is designed as convenient way to take notes, allows for files to be embedded as attachments as well as executed from OneNote.
Some of these file types include:
- Documents
- Videos
- Audio Clips
- Batch Scripts
- HTA (HTML Applications)
- JS (JavaScript)
- WSF (Windows Script File)
- VBS (Visual Basic Script)
A tool that was intended for ease of use and convenience has quickly spiraled into an attack vector being used by threat actors.
In the next image we look at a deobfuscated back script which was found embedded in one of the samples analyzed by Blackpoint Cybers SOC.
We see that the script download a file called 01.gif, saves it as a putty.jpg and executes it with rundll32.exe. It was also observed that automation in the payload generation is being used by the threat actor.
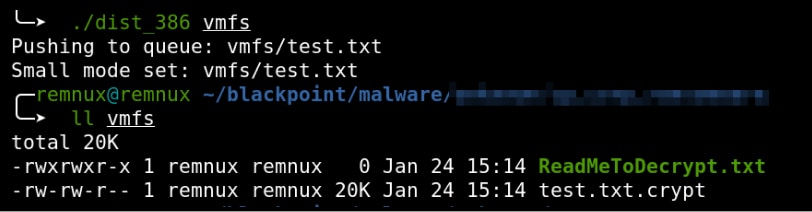
The generated putty.jpg file is actually a Dynamic Link Library (DLL) which is masquerading as an image file to evade detection. Once run, rundll32.exe loads the putty.jpg file as a module and the following processes are created before its own process is killed:
- wermgr.exe (Windows Problem Reporting)
- rundll32.exe injected shellcode into wermgr.exe using process hollowing, which is a technique that hides malicious code inside a legitimate process
- msra.exe (Microsoft Remote Assistant)
- Sets multiple registry keys under “HKCU\Software\Microsoft\Yerqbqokc\”
- Creates SearchProtocolHost.exe thread (which is an index of your filesystem)
- Queries values from multiple registry keys listed above
- svchost.exe (Service Host)
- Sets multiple registry keys under “HKLM\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Schedule\TaskCache\Tasks\”
- Modifies Windows Update Orchestrator
The malware samples collected from OneNote attacks by Blackpoint’s SOC have identified these attacks to be Qakbot attacks due to the Indicators of Compromise (IoC) matching already known Qakbot attacks. This was determined by Antivirus detection, YARA rules, and the Adversary Pursuit Group (APG).
Qakbot is know for process injection into legitimate processes and the use of “Wind” as an exported function in their DLL’s.
To Summarize
The execution of such embedded payloads in OneNote can have various outcomes depending ont he intent of the threat actor. Analysis carried out by the Adversary Persuit Group (APG) shows that this particular attack had two main aims:
- To establish persistence in the registry and scheduled tasks.
- To setup ufurther payload delivery and C2 interactions.
Depending on the threat actors, they could leverage OneNote as a means to carry out a ransomware attack or something more complex. At this time manual user interaction in the form of double clicking on one of the embedded files is required to start the attack since OneNote has no built in automatic execution mechanisms.
It is essential to remain on guard when dealing with suspicious files to ensure you do not fall victim to such an attack.
Reference:
https://blackpointcyber.com/resources/blog/with-one-foot-in-the-door/
Leave a Reply