Dragos, a cybersecurity firm specializing on protecting the industrial space, on May 8th 2023 had a cyber criminal group attempt an extortion scheme which ultimately failed. In this post we will look at how to deconstruct a cybersecurity incident. We will also look at how important it is to understand the sequence of events, identify the root cause, and carry out an in depth investigation to properly respond and recover from such an event. It is important to take a holistic approach as a wide variety of technical expertise is needed for incident response planning as well as collaboration between the various teams. We will look into the various steps of a cyber security incident which include information gathering, analysis and remediation strategies. It is important to note as well that a proactive response to an incident as well as continuous improvement will only serve to enhance an organizations cybersecurity posture.
The incident started when a cyber criminal group managed to access and compromise the personal email address of a new employee joining our sales team prior to their first day on the job. They in turn used this information to impersonal the employee and go through the first day onboarding process. With this access that a new sales employee would have, they accessed SharePoint and the Dragos Contact Management System. In one case, a report was received that had an IP Address of a customer was accessed and the customer was contacted.
Alerts in the SIEM, or Security Information & Event Management System, were investigated and the account in question was blocked. Dragos activated their incident response retainer they have with Crowdstrike & also engaged their 3rd party MDR, or Monitoring, Detection & Response, provider to manage the response efforts. Given that Dragos have layered security controls in place this prevented the threat actor from achieving their goal of initiating a ransomware attack. They were also prevented from any lateral movement, privilege escalation, establishing persistence to the Dragos infrastructure and making any infrastructure changes.
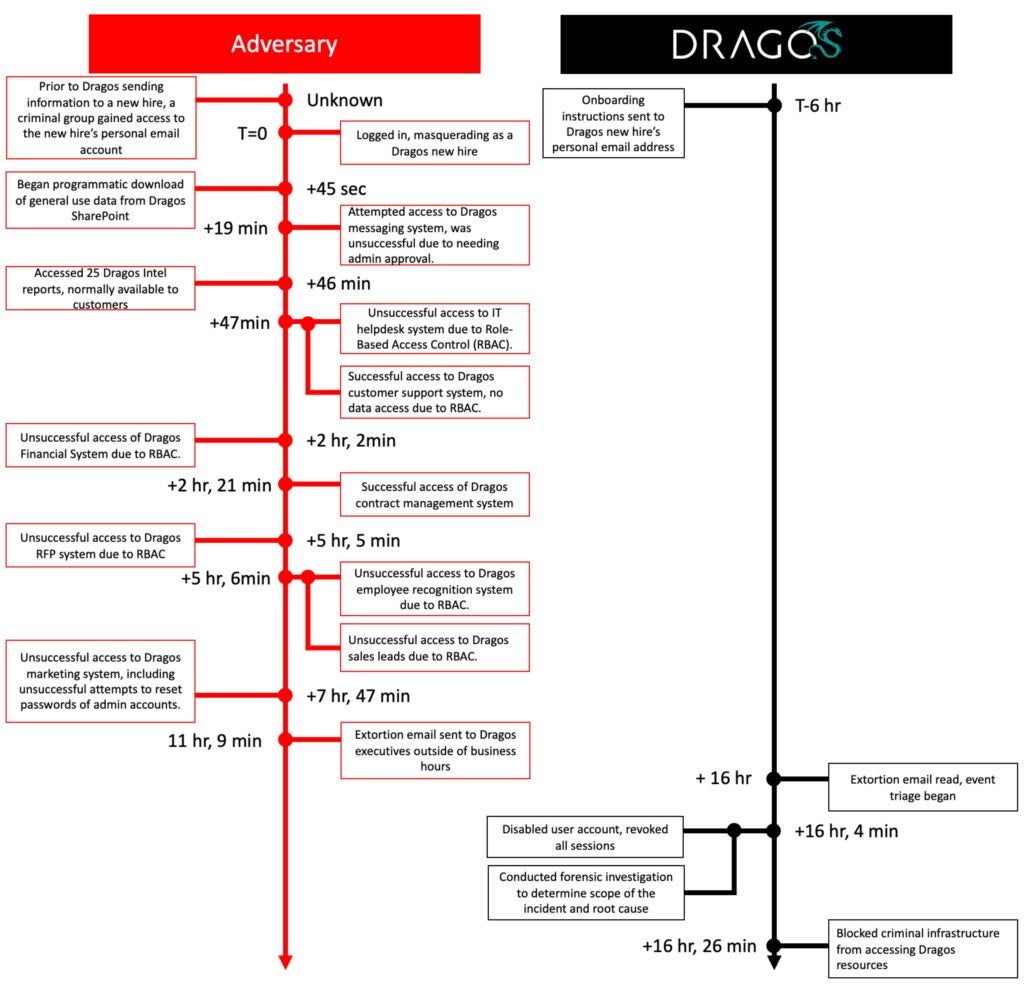
Attack Timeline
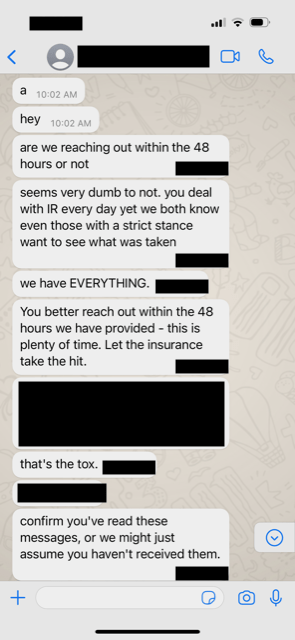
The known motive of this cyber criminal group is that of deploying ransomware. When their attempts failed to gain control of Dragos systems so they could deploy ransomware, they pivoted to extortion attempts to various Dragos executives to try and avoid disclosure to the public. Here is one such example of messages that were sent to Dragos executives:
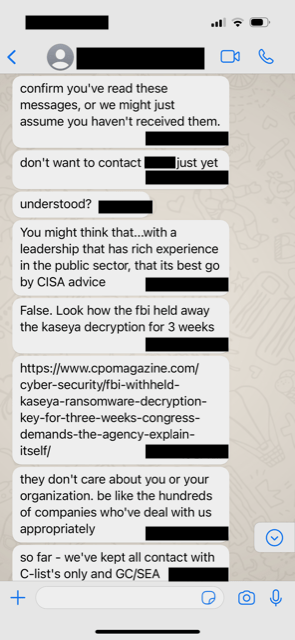
They then proceeded to expand their tactics to include references to family members and personal contacts.
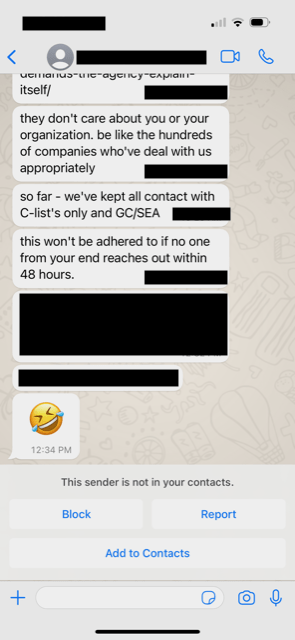
Escalation continued but none of the contacted Dragos Executives engaged.
They kept reaching out to a handful of publicly known Dragos employees in an attempt to get a response
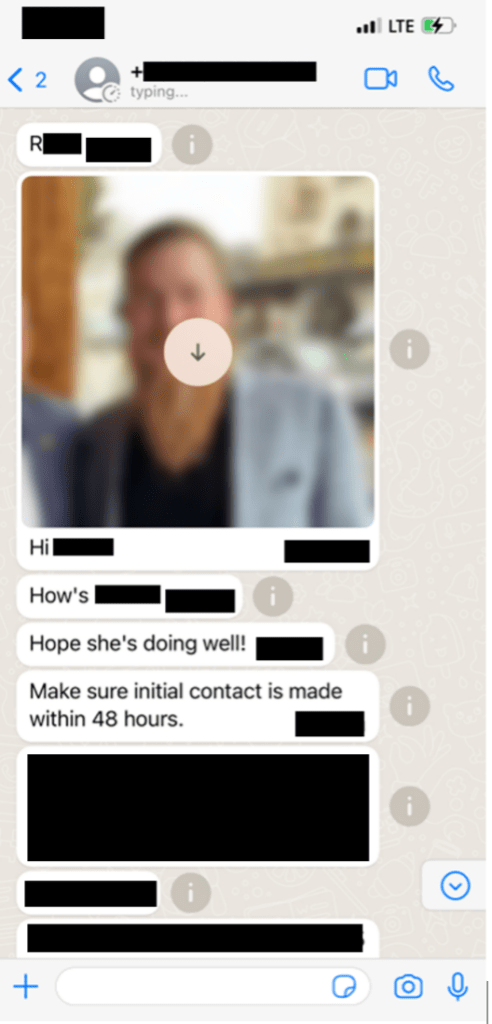
The scary part of what these cyber criminal’s texts show is that they did a fair bit of research into the names of family members of Dragos Executives, but when it came to them referencing emails, fictitious ones were used. On top of the messages to executives, employees were also emailed on their personal email addresses.
It was the best option for any employees or executives that were contacted by these criminals to not respond or engage with them.
While the external incident response firm and Dragos analysts feel the event is contained, but there is an ongoing investigation.
MITRE ATT&CK Map
| Tactic |
Technique |
Procedure |
| TA0001 |
T1078 |
Leverage Valid Accounts |
| TA0006 |
T1621 |
Multi-Factor Authentication Request Generation |
| TA0007 |
T1526 |
Cloud Service Discovery |
| TA0009 |
T1530 |
Collect Data from Cloud Storage |
| TA00010 |
T1567 |
Exfiltration Over Web Service |
| TA0042 |
T1586.002 |
Compromise Email Accounts |
| TA0043 |
T1593 |
Search Open Websites/Domains |
|
T1591.004 |
Gather Victim Org Information: Identify Roles |
Click here to search and read more about the attack techniques used.
IOC (Indicators Of Compromise)
Two IP addresses were observed to be behind this attack.
- 144[.]202[.]42[.]216
- 162[.]33[.]179[.]126
The email address being used by these attackers was the following:
- dragos.negotiations[@]proton.me
Lessons Learned by Dragos & Further Security Enhancements
As lessons learned by Dragos from this incident are the following:
- Implemented additional verification steps to additionally harden the onboarding process so a repeat attack cannot happen again.
- Every thwarted access attempts were due to having a multiple step access approval. Evaluation is ongoing increasing the use of additional control based access depending on system criticality.
- Due to the positive outcomes of not engaging or negotiating with the cyber criminals made their resolve stronger.
- Lastly the verbose nature of the activity logs enabled Dragos to rapidly contain and triage the security incident.
Some further security recommendations that Dragos is looking into after this security incident are as follows:
- Further harden Identity & Access management (IAM) infrastructure and their respective processes.
- Implement seperation of duties across the enterprise.
- Adopt Zero trust principles, principle of least privilege to all systems and services.
- Ensure MFA (Multi-factor Authentication) is implemented where ever possible.
- Explicitly block known bad IP Addresses, like those mentioned earlier.
- Implement stronger spam filtering on incoming emails for the usual phishing triggers which also include email address, URL and spelling filtering.
- Lastly Ensure continuous security monitoring is running with properly tested incident and response playbooks.
Reference:
https://www.dragos.com/blog/deconstructing-a-cybersecurity-event/ 
 The known motive of this cyber criminal group is that of deploying ransomware. When their attempts failed to gain control of Dragos systems so they could deploy ransomware, they pivoted to extortion attempts to various Dragos executives to try and avoid disclosure to the public. Here is one such example of messages that were sent to Dragos executives:
The known motive of this cyber criminal group is that of deploying ransomware. When their attempts failed to gain control of Dragos systems so they could deploy ransomware, they pivoted to extortion attempts to various Dragos executives to try and avoid disclosure to the public. Here is one such example of messages that were sent to Dragos executives:
 They then proceeded to expand their tactics to include references to family members and personal contacts.
They then proceeded to expand their tactics to include references to family members and personal contacts.
 Escalation continued but none of the contacted Dragos Executives engaged.
Escalation continued but none of the contacted Dragos Executives engaged.
 They kept reaching out to a handful of publicly known Dragos employees in an attempt to get a response
They kept reaching out to a handful of publicly known Dragos employees in an attempt to get a response
 The scary part of what these cyber criminal’s texts show is that they did a fair bit of research into the names of family members of Dragos Executives, but when it came to them referencing emails, fictitious ones were used. On top of the messages to executives, employees were also emailed on their personal email addresses.
It was the best option for any employees or executives that were contacted by these criminals to not respond or engage with them.
While the external incident response firm and Dragos analysts feel the event is contained, but there is an ongoing investigation.
The scary part of what these cyber criminal’s texts show is that they did a fair bit of research into the names of family members of Dragos Executives, but when it came to them referencing emails, fictitious ones were used. On top of the messages to executives, employees were also emailed on their personal email addresses.
It was the best option for any employees or executives that were contacted by these criminals to not respond or engage with them.
While the external incident response firm and Dragos analysts feel the event is contained, but there is an ongoing investigation.
 The known motive of this cyber criminal group is that of deploying ransomware. When their attempts failed to gain control of Dragos systems so they could deploy ransomware, they pivoted to extortion attempts to various Dragos executives to try and avoid disclosure to the public. Here is one such example of messages that were sent to Dragos executives:
The known motive of this cyber criminal group is that of deploying ransomware. When their attempts failed to gain control of Dragos systems so they could deploy ransomware, they pivoted to extortion attempts to various Dragos executives to try and avoid disclosure to the public. Here is one such example of messages that were sent to Dragos executives:
 They then proceeded to expand their tactics to include references to family members and personal contacts.
They then proceeded to expand their tactics to include references to family members and personal contacts.
 Escalation continued but none of the contacted Dragos Executives engaged.
Escalation continued but none of the contacted Dragos Executives engaged.
 They kept reaching out to a handful of publicly known Dragos employees in an attempt to get a response
They kept reaching out to a handful of publicly known Dragos employees in an attempt to get a response
 The scary part of what these cyber criminal’s texts show is that they did a fair bit of research into the names of family members of Dragos Executives, but when it came to them referencing emails, fictitious ones were used. On top of the messages to executives, employees were also emailed on their personal email addresses.
It was the best option for any employees or executives that were contacted by these criminals to not respond or engage with them.
While the external incident response firm and Dragos analysts feel the event is contained, but there is an ongoing investigation.
The scary part of what these cyber criminal’s texts show is that they did a fair bit of research into the names of family members of Dragos Executives, but when it came to them referencing emails, fictitious ones were used. On top of the messages to executives, employees were also emailed on their personal email addresses.
It was the best option for any employees or executives that were contacted by these criminals to not respond or engage with them.
While the external incident response firm and Dragos analysts feel the event is contained, but there is an ongoing investigation.
Leave a Reply