
On 29th March 2023, the popular VoIP communications system used by businesses worldwide, 3CX, has reportedly been targeted in a supply chain attack. A digitally signed legitimate version of the desktop softphone has been weaponized and is reportedly being used to target its customers in an ongoing supply chain attack.
3cx is a modern day IPBX (Internet Protocol Private Branch Exchange) whose company has their phone system used globally by over 600,000 companies with 12 million daily users.
3cx has a long list of high profile companies. Some of these companies include:
- American Express
- Coca-Cola
- McDonald’s
- BMW
- Honda
- Air France
- NHS
- Toyota
- Mercedes-Benz
- Ikea
- Holiday Inn
Security researchers from Sophos and CrowdStrike raised the alarm that the attackers are targeting both windows and mac users that are using the compromised version of the desktop softphone application.
What was noted by the CrowdStrike Threat intel team and I quote the following:
“The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads and in a small number of cases hands-on-keyboard activity.”
The Sophos Managed Detection and Response Service added, and I quote the following:
“The most common post exploitation activity observed to date is the spawning of an interactive command shell.”
It is suspected by CrowdStrike that North Korean Stated back hacking group they track as Labyrinth Chollima, but researchers at Sophos are not confident in this attribution. This group overlaps with other threat actors with other threat actors which are tracked as Lazarus Group by Kaspersky, Covellite by Dragos, UNC4034 by Mandiant, Zinc by Microsoft and Nickel Academy by Secureworks.
This group is a subset of what has been described as Lazarus Group. This includes other DPKR-nexus adversaries including Silent Chollima and Stardust Chollima.
How does the 3CX Supply ChainAttack Work
Dubbed by SentinalOne this supply chain attack is known as ‘SmoothOperator’ and starts when the MSI installer is downloading from the 3cx website or through an update pushed out via the pbx system to systems that have the application already installed.
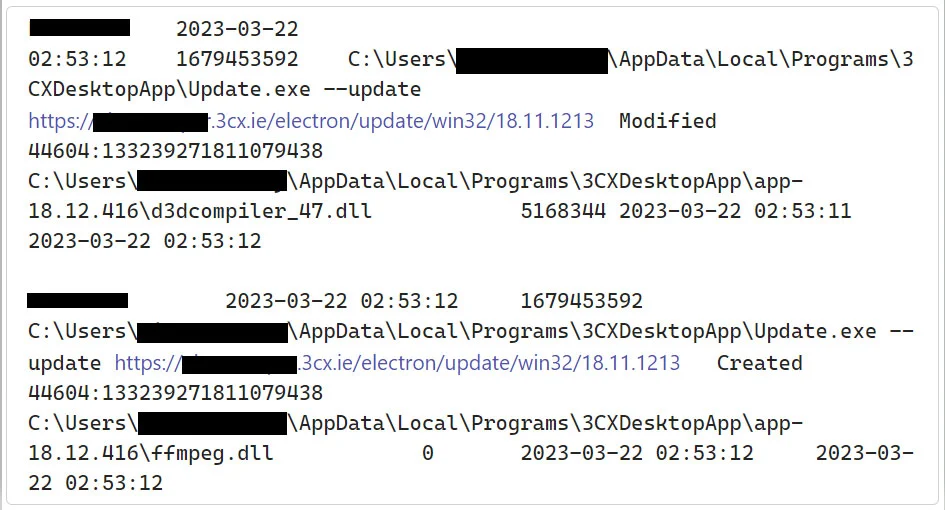
Update process installing the malicous files (Sophos)
When the installer is run or update installed a malicious ffmpeg.dll and d3dcompiler_47.dll get installed on the machine. These files are used in the next stage of the attack.
According to Sophos the executable is not malicious, but what is are the DLL’s. These are side loaded and in turn extract an encrypted payload from the d3dcompiler_47.dll and executes it.
As explained by SentinelOne the malware at this point downloads icon files that are hosted on GitHub. These icons contain a Base64 encoded string that are appended
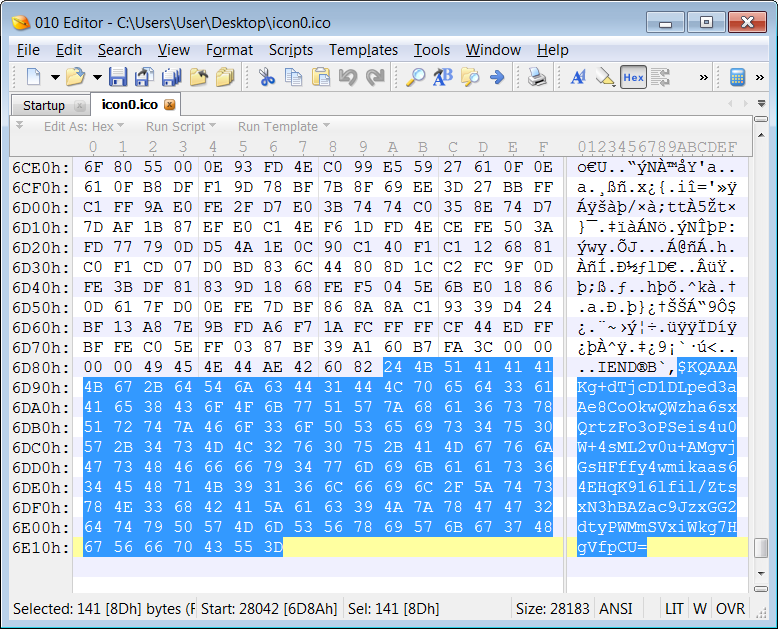
Base64 strings embedded in ICO files (BleepingComputer)
The GitHub respository where these icons are stored shows that the first icon was uploaded on 7th of December 2022.
The first stage of this malware uses the Base64 strings in the icon files to download the final payload to the compromised devices, this is in the form of a previously unknown malware strain which is downloaded as a DLL. This new malware is capable of harvesting system information and stealing data and stored credentials from Chrome, Edge, Brave, and Firefox user profiles.
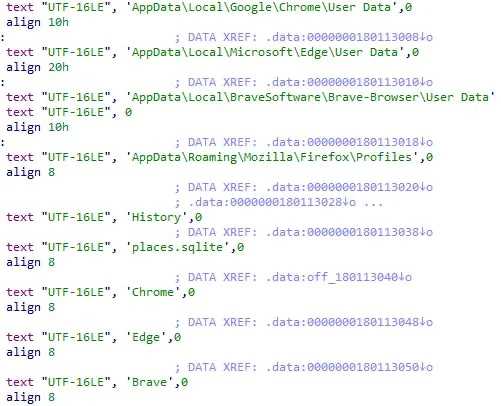
Data targeted in SmoothOperator supply chain attack (SentinelOne)
According to CrowdStrike, the compromised version will reach out to the following domains:
| akamaicontainer[.]com | msedgepackageinfo[.]com |
| akamaitechcloudservices[.]com | msstorageazure[.]com |
| azuredeploystore[.]com | msstorageboxes[.]com |
| azureonlinecloud[.]com | officeaddons[.]com |
| azureonlinestorage[.]com | officestoragebox[.]com |
| dunamistrd[.]com | pbxcloudeservices[.]com |
| glcloudservice[.]com | pbxphonenetwork[.]com |
| qwepoi123098[.]com | zacharryblogs[.]com |
| sbmsa[.]wiki | pbxsources[.]com |
| sourceslabs[.]com | journalide[.]org |
| visualstudiofactory[.]com |
Multiple customers have stated that they have been getting alerts starting on the 22nd of March 2023 stating that it has been marked as malicious by SentinalOne, CrowdStrike, ESET, Palo Alto Networks & SonicWall. They also said that these alerts were triggered after version 18.12.407, and 18.12.416 on windows as well as 18.11.1213 on mac were installed.
One of the malicious samples shared by CrowdStrike was digitally signed 3 weeks ago on March 3rd 2023 with a legitimate 3cx certificate that was issue by DigiCert.
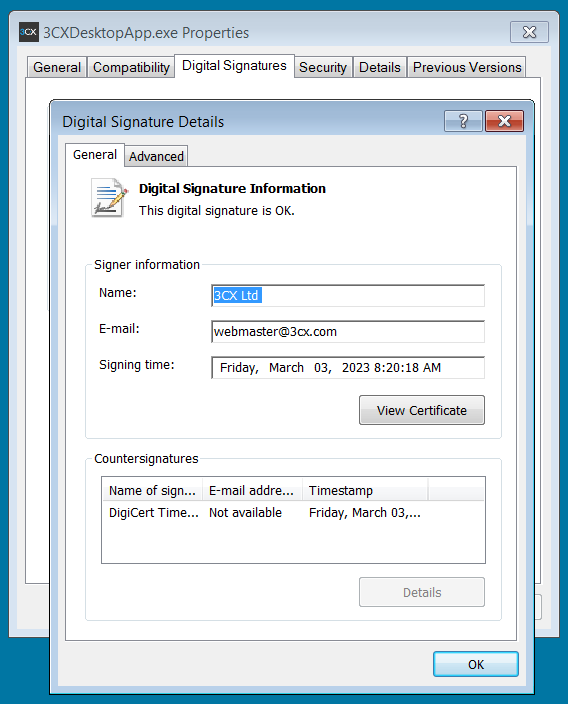
Analysis of the compromised binary
In analysis of the compromised binary, SentinalOne detects a penetration framework or shell code, ESET tags it as Win64/Agent.CFM trogan, Sophos as Troj/Loader-AF, and CrowdStrike Falcon Overwatch managed threat hunting service warns users to investigate their systems for malicious activity urgently.
Initially 3cx support team members tagged this as a potential false positives in SentinalOne on Wednesday even though there were a large number of reports on the forums.
Thursday morning via the 3cx forums CEO Nick Galea confirmed that the Desktop Application was compromised to include malware (Forum Post).
As an alternative the Progressive Web Application (PWA) is being recommended instead. The version of the desktop app that is effected is the Windows Electron client for customers that are currently 3cx version 18 update 7.
To ensure systems are kept safe, they recommend uninstalling the desktop application at this time.
CISO Pierre Jourdan states that the compromise happened due to an upstream library. He states that they are still looking into the matter to provide a more detailed response.
As of right now 3cx has not shared what libraries they are referring to which led to their developer environment being compromised.
We at EagleEyeT are here to assist if you have any questions do not hesitate to leave a comment down below or reach out to us if you need any assistance.
REFERENCES:
Bleeping Computer – Hackers Compromise 3cx Desktop App In Supply Chain Attack
Leave a Reply