Networks Breach Exposes BIG-IP Source Code: What It Means for Enterprise Security
In a major cybersecurity incident shaking the enterprise infrastructure world, F5 Networks, the company behind the widely used BIG-IP application delivery and security solutions, has confirmed a data breach exposing…
Read moreTruist Bank’s $4.1M TCPA Settlement: What Businesses Need to Know About Robocall Compliance
In today’s digital world, reaching customers by phone can be a powerful marketing tool, but it comes with significant legal risks. The recent Truist Bank TCPA settlement, a $4.1 million…
Read moreTCPA Guidelines for Beginners: Best Practices to Stay Compliant
The Telephone Consumer Protection Act (TCPA) sets strict rules on how businesses can contact consumers by phone, text, and fax. If you’re new to the world of marketing compliance, understanding…
Read moreGitLab Patch Release: 18.4.2, 18.3.4, and 18.2.8 — Critical Security Fixes You Should Apply Now
On October 8, 2025, GitLab announced the release of versions 18.4.2, 18.3.4, and 18.2.8, a patch rollout designed to address multiple security and maintenance issues in both Community (CE) and…
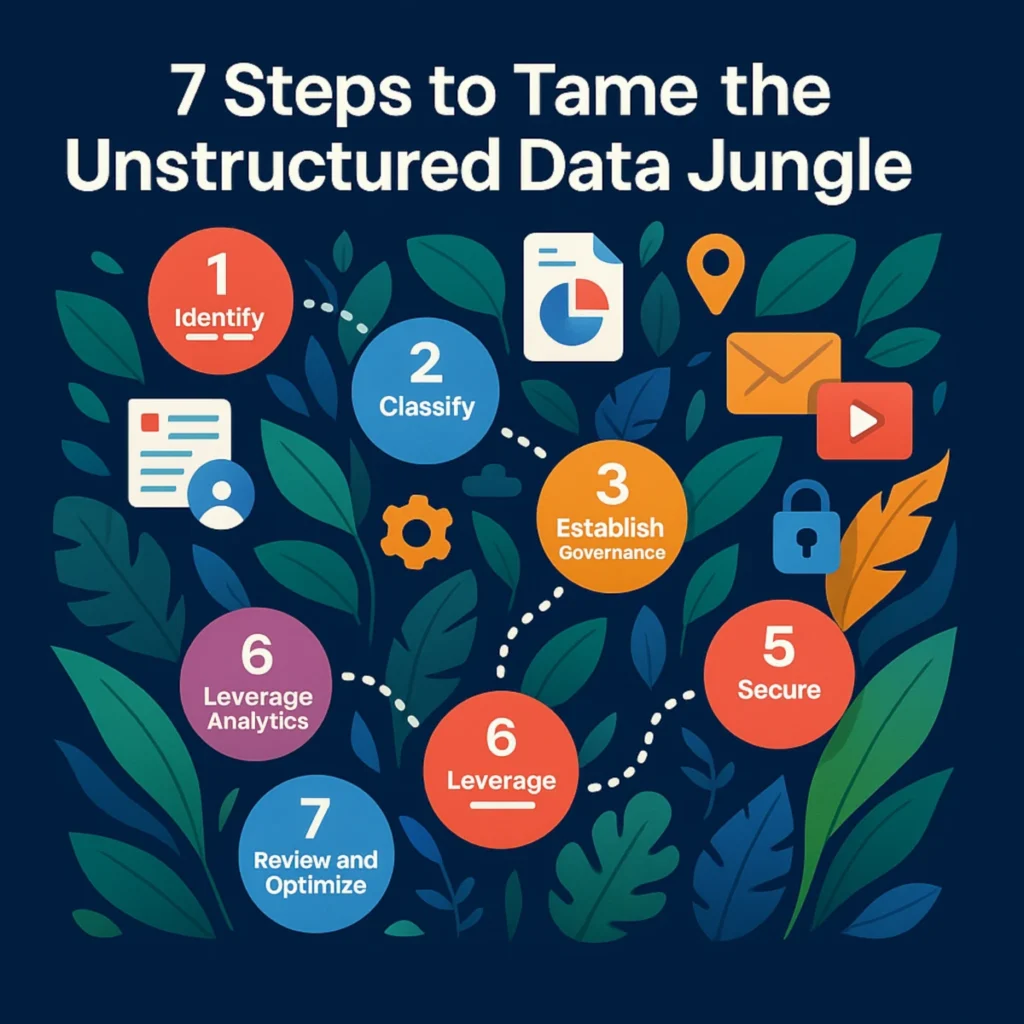
Read moreMastering Unstructured Data: 7 Steps to Tame the Jungle in 2025
Unstructured data from emails and documents to videos, images, and social media now accounts for more than 80% of business information. But without proper management, this vast data “jungle” can…
Read moreBeyond the Inbox: What Discord’s Zendesk Breach Reveals About Third-Party Risk (and Your Data)
The Discord Zendesk breach is a textbook example of how supply chain risks can hit even massive platforms: attackers didn’t break into Discord’s core systems they compromised a third party…
Read moreGoogle’s Revolutionary AI Can Now Rewrite Code to Fix Security Flaws Automatically
In a major breakthrough for cybersecurity and software engineering, Google’s latest AI innovation doesn’t just find vulnerabilities, but rewrites the code to fix them automatically. Unveiled in October 2025, this…
Read moreHow to Install GitLab on Debian 12 (Bookworm): Complete Step-by-Step Guide
If you’re running Debian 12 (Bookworm) and want a powerful self hosted Git platform, GitLab Community Edition (CE) is one of the best choices. It combines source code management, CI/CD…
Read moreProxmox vs VMware vs Hyper-V: How Proxmox Stacks Up Against Mainstream Virtualization Platforms
When it comes to server virtualization, IT professionals have plenty of options. The most well known enterprise platforms are VMware vSphere, Microsoft Hyper-V, and Citrix Hypervisor which dominate much of…
Read moreThe Pikachu Virus: How a Pokémon Email Scam Sparked 25 Years of Cybersecurity Lessons
In June 2000, at the height of Pokémon mania, the Pikachu virus became one of the first email based malware outbreaks to capture global attention. Disguised as a harmless Pokémon…
Read more