
Trojans are similar to that of armies and actually behave in the same way. Armies usuallly send out the scouts first to survey the area and ensure all is ok. Once that is done the heavy troops can be sent in. This is how things were prior to the age of cyber warfare.
In this article we will look at the Tirada malware strain and dissect it to help you better understand its capabilities.
A lot of small trojans exist in the Android space which have the capabilities of taking advantage of access privileges, which is another way to say they can gain root access.
Kaspersky malware analysts Nikita Buchka & Mikhail Kuzin can name 11 families of such trojans. Most are harmless and until recently all they did was inject alot of ads and downloaded other trojans. If you would like to read more into detail about these families their article can be found by clicking on this link.
Keeping with the army analogy that we used at the beginning of this post, trojans are the scouts. Once the trojans gain root access this gives them the ability to download and install applications.
Once you have one on your device it is only a matter of a couple of minutes before you will have all the others on your device as well.
Kaspersky researchers predicted that these small trojans could certainly be used to download some extremely bad malware that could potentially harm the owners of those infected devices.
this is what recently happened. Some of the small trojans such as Leech, Ztorg, and Gopro now download the most advanced mobile Trojan Kaspersky malware analysts have ever encountered known as Tirada.
Tirada is a modular mobile Trojan that uses root privileges to substitute system files. It exists mainly the devices RAM which makes it really hard to detect.

Tirada & Its Dark Ways
Once the trojan is downloaded and installed, the Tirada trojan attempts to collect some information about the victim device. Some of the information gather includes the model of the device model, Android version, amount of space on the SD card, the list of installed applications and other information.
All this information is sent back to the Command & Control server (C2). Kaspersky have detected around 17 such servers operating on 4 different domains. This probably means that those behind the malware are aware of what redundancy is.
The C2 server in turn will respond with a configuration file that contains the personal identification number (PIN) for the device and some settings such as the time interval between contacting the server, the list of modules to be installed etc.
After the modules get installed they are then deployed to the short term memory and deleted from the device storage which makes it increasingly hard to catch.
Another two reasons exist as t why Tiradais really hard to detect and why Kaspersky researchers were impressed by it.
The first thing it does is modify the zygote process. This is the core process in Android that is used as a template for all applications. What this means is that once the Trojan infiltrates this process it literally is a part of ever app that is launched on the device.
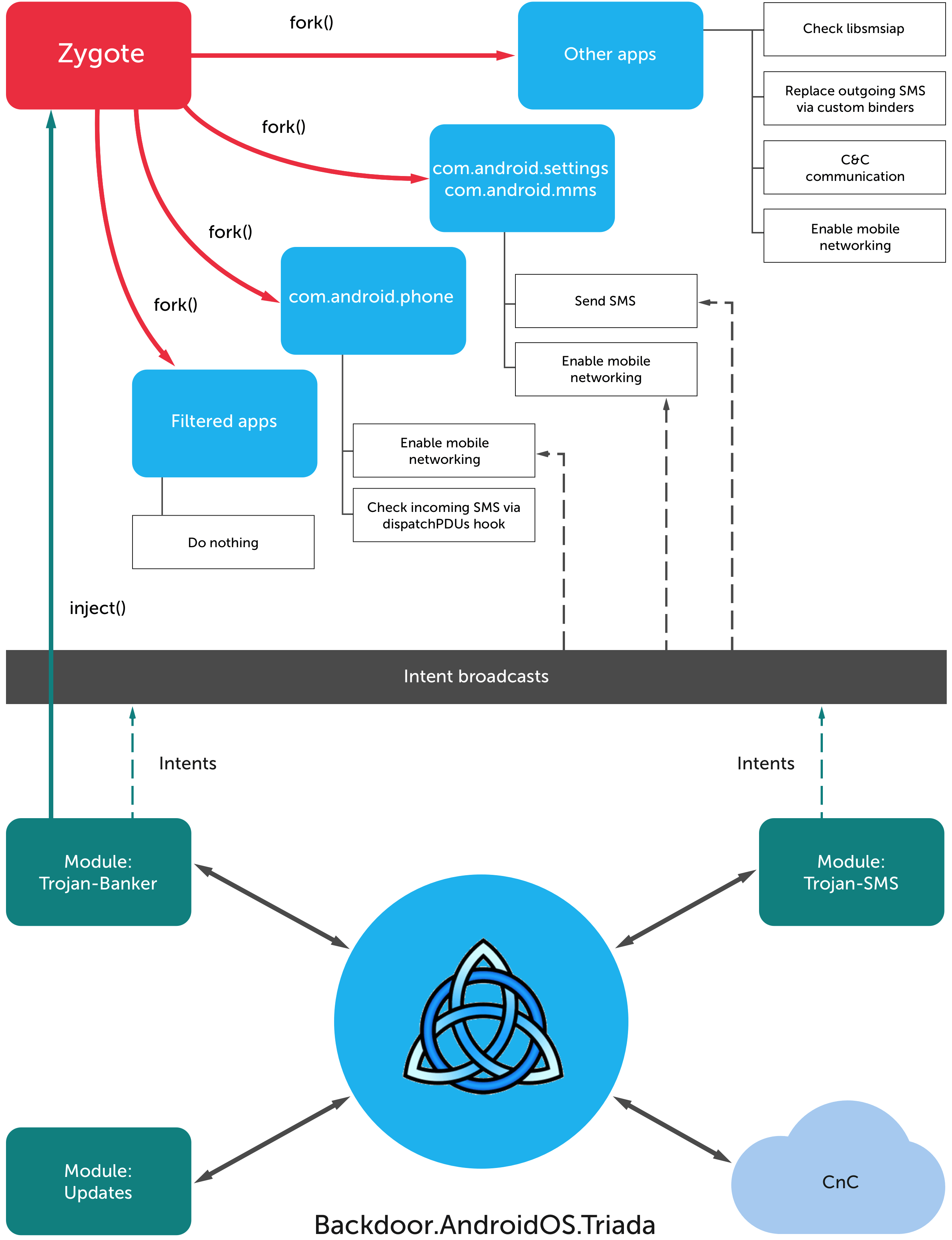
After attaching itself to the zygote process it then moves to substitute system functions and conceal its modules from the list of running processes and installed apps. This is so that any strange processes that are running do not trigger any alarms.
Tirada does not only modify the above, it also lays the ground work on outgoing SMS messages and filters the incoming ones. This is how the malicious threat actors decided to monetize the trojan.
There are some applications which rely on SMS messages when it comes to in app purchases. Transaction data is transferred via short text message.
The reason developers go for this over standard payments via the internet is that SMS’s do not require an internet connection.
Users do not see such messages as they are not processed by the Message app, but by the app itself such as a free to play game.
The functionality of Tirada allows it to modify those silent messages so that the money does not go to the app developers but those operating the malware.
It steals money either from the users, if they didn’t succeed to make the purchase they wanted, or from the app developer in case a purchase is completed successfully.
Right now this is the only way the cybercriminals can make money off of tirada. It is important to remember that this trojan is modular and from the C2 server it can be turned into anything by issuing a command.
Using Your Phone To Fight Organized Crime
The biggest problem with Tirada is that it can hurt lots of people.
As previously mentioned Tirada downloads smaller Trojans that take advantage of access privileges.
Kaspersky researchers estimate that for every 10 Android users 1 was attacked by either one or several trojans in the 2nd half of 2015. This means that there are millions of devices with the huge possibility that they might be infected with Tirada.
What Can You Do To Protect Yourself From The Stealthy Beast Tirada?
A few simple steps can be followed to protect you from Tirada.
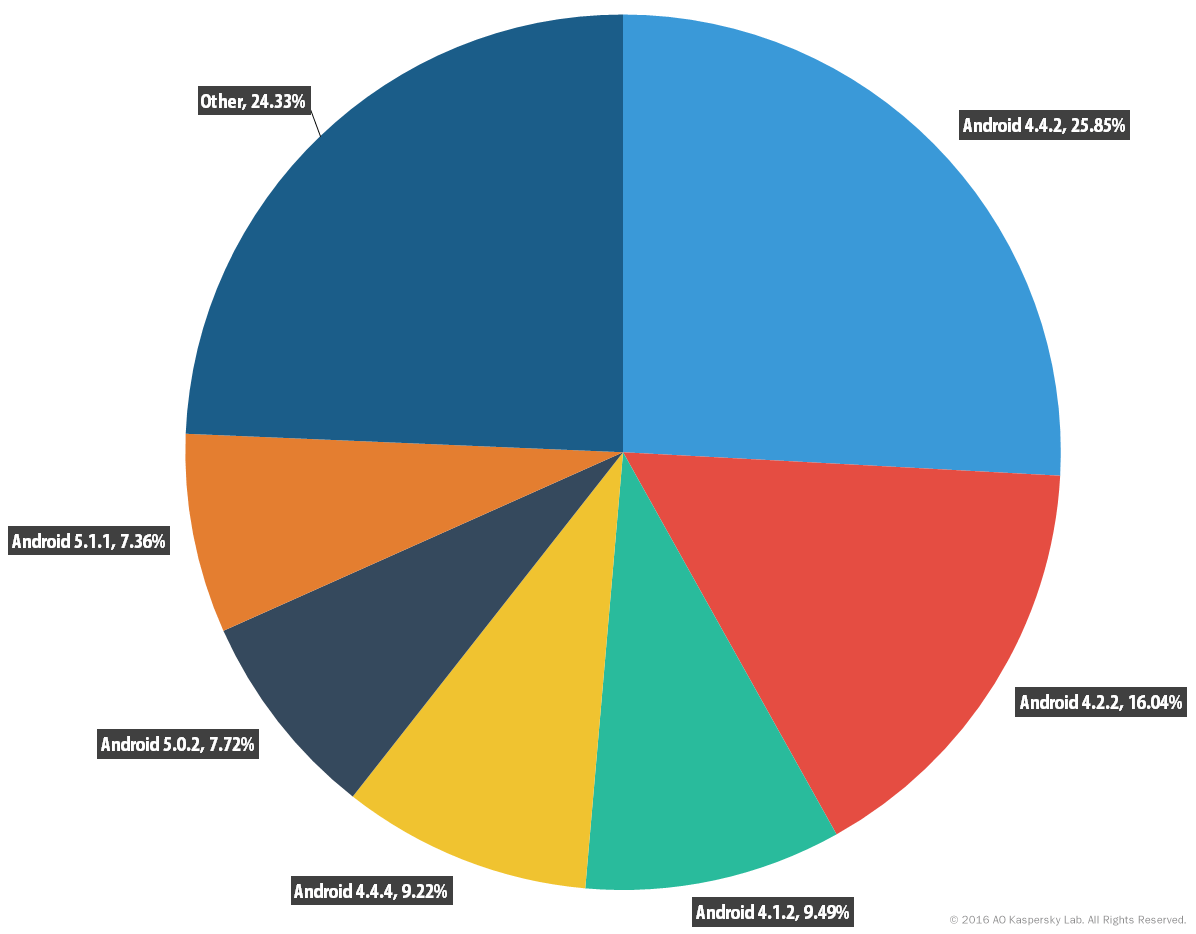
Keep your device up to date. It seems like the smaller Trojans have a major problem getting root access on Android version 4.4.4 and higher since a lot of vulnerabilities had been patched in these versions.
If you have Android version 4.4.4 or newer on your device this significantly lowers your chance of getting infected by Tirada.
Statistics by Kaspersky show that around 60% of Android users still have Android version 4.4.2 and lower.
If you do not want to take any chances regardless of what Android version you are on it is best to install an antivirus solution on your device.
Antivirus solutions will detect all 3 Tirada modules so it can keep your money out of the hands of the cyber criminals.
Manual scans would need to be run as they do not do so automatically on free versions.
To conclude, Tirada is another example of a really bad trend that is currently taking place. Malware developers are really focusing on Android and as it can be seen the latest malware samples are as complex and hard to protect against as their windows brothers.
The only good way to fight such threats is to take a proactive approach and a good security solution is a must.
Leave a Reply