Security incidents no longer unfold neatly, but sprawl across identity...
Read More
The Discord Zendesk breach is a textbook example of how supply chain risks can hit even massive platforms: attackers didn’t break into Discord’s core systems they compromised a third party customer service environment and exfiltrated sensitive support data. Discord now says about 70,000 users’ government-ID photos may have been exposed, while the threat group claims a much bigger haul. We break down the facts, the claims, and the practical steps you should take right now.
What Happened?
- Vector: Attackers accessed Discord’s customer support stack by compromising a support agent account connected to Zendesk via an outsourced BPO provider not Discord’s production infrastructure.
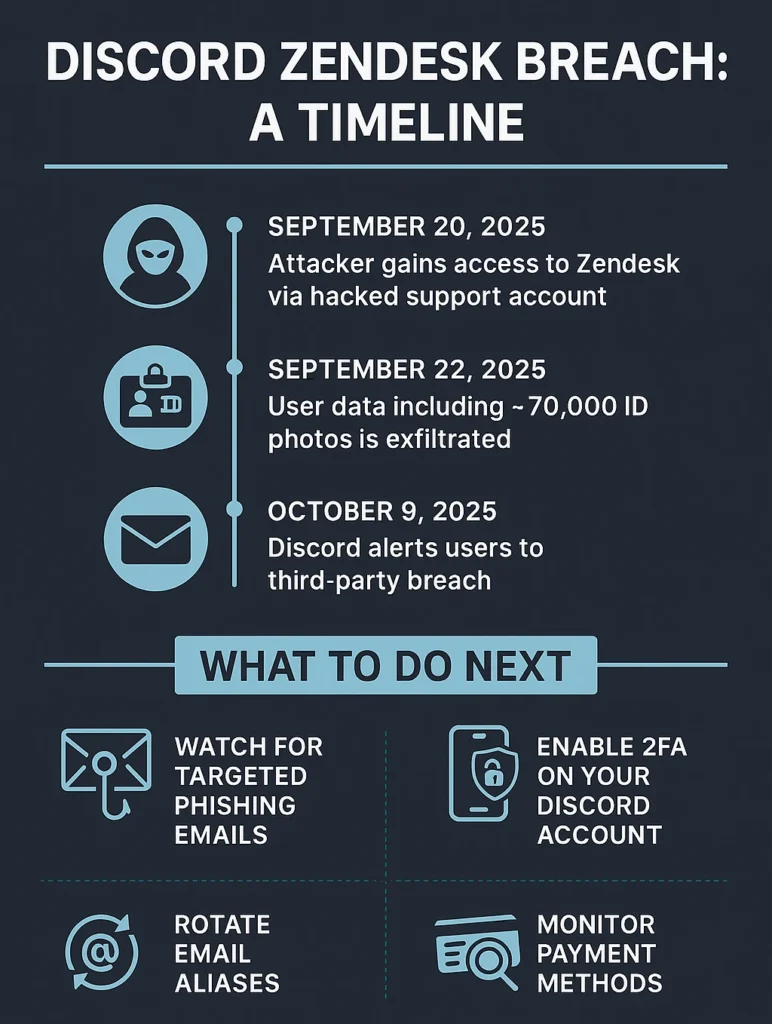
- Window of access: ~58 hours beginning September 20, 2025 (per the threat actor’s account).
- Discord’s confirmation: Discord disclosed a third party support incident and emphasized it wasn’t a breach of Discord’s own systems; later public statements tied the incident to Zendesk/outsourced support.
What Data Was Exposed?
Discord’s statement (confirmed)
- Gov-ID images submitted for age-verification appeals (≈ 70,000 users).
- Support data for users who contacted Customer Support / Trust & Safety (names, usernames, emails, IPs, limited billing metadata like last 4 digits, purchase history).
- No passwords or core account credentials were compromised.
Threat actor’s claims (disputed)
- 1.5–1.6 TB of data, including ~2.1 million ID photos and 8.4M support tickets touching 5.5M users; ransom demands reportedly varied between $5.5M and $3.5M. Discord calls this exaggerated/extortionate and says it will not pay.
How the Attack Allegedly Worked
- Initial access: Compromise of a BPO support agent account (phishing or credential abuse) allowed for access to Discord’s internal Zendesk instance.
- Support tooling: Actor claims access to a tool (“Zenbar”) capable of sensitive lookups and certain support actions.
- Exfiltration: Bulk download of ticket transcripts and attachments (including ID images).
- When third party agents hold broad support permissions, a single compromised identity can translate into high impact data exposure.
Who Is Affected?
- Users who opened tickets with Discord Support/Trust & Safety, especially those who submitted ID documents for age verification appeals.
- Discord says it notified affected users and cut ties with the compromised vendor and is working with law enforcement.
Immediate Steps You Should Take
- Watch for targeted phishing. Expect convincing emails referencing real support tickets. Don’t click links; go directly to discord.com or the app.
- Enable 2FA (preferably TOTP or a hardware key). Avoid SMS when possible.
- Rotate email aliases used with Discord if you receive unusual login prompts or social engineering attempts.
- Monitor payment methods. While full card numbers weren’t exposed, keep an eye on statements; consider refreshing stored cards.
- If you submitted an ID: Consider freezing your credit (where available), and be alert to identity verification scams that reference Discord.
What Discord (and Everyone Using CRMs) Should Do Next
- Least privilege for support agents: Granular roles; break glass only with approvals.
- Short lived, device bound credentials: Enforce phishing resistant MFA (FIDO2) for agents and vendors.
- Data minimization & retention: Avoid storing ID images unless legally required; adopt attachment vaulting with strict expiry.
- Exfiltration controls: DLP on ticket attachments, anomaly detection on bulk downloads.
- Vendor risk management: Continuous control monitoring of BPOs/CRMs; tabletop exercises for third party incidents.
These controls map to modern supply chain guidance used across the industry.
The Bigger Picture: Supply Chain and CRM Breaches
Discord’s incident joins a pattern of CRM/help desk compromises where attackers chase the richest user data outside a company’s core. Security teams should treat support platforms as crown jewel adjacencies because to an attacker, sensitive attachments and verified identity documents are just as valuable as primary databases.
Conclusion
The Discord Zendesk breach underscores a hard truth: your security posture is only as strong as the least-protected vendor account with access to your users’ sensitive data. While Discord asserts the scope is ~70,000 ID photos, far below the attackers’ claims, the incident is a wake up call to harden support ecosystems, constrain third party access, and minimize long lived sensitive data.
If you’ve interacted with Discord support recently, assume targeted phishing risk is elevated and take the precautions above.
Sources
- The Verge — Discord says 70,000 users may have had government IDs leaked in breach
- Tom’s Hardware — Discord confirms ~70,000 ID photos exposed; rejects ransom claims
- Discord — Update on a Security Incident Involving Third-Party Customer Service
- BleepingComputer — Threat actor claims access to Discord’s Zendesk for 58 hours
- SOCRadar — Discord Zendesk Breach: What We Know So Far
- Malwarebytes — Discord warns users after data stolen in third-party breach
- The Guardian — Hack of age verification firm may have exposed 70,000 Discord users’ ID photos
The Singularity Defines the Incident Command Maturity Model
🚨 Incident response doesn’t fail because of missing tools —...
Read MoreThe Singularity’s Guide To Creating Strong Passwords And Keeping Them Secure
🔐 Weak passwords are still one of the biggest security...
Read MoreThe Singularity On How To Prevent Cyber Attacks
Cyber attacks don’t start with malware — they start with...
Read More



Leave a Reply