
On May 11th 2023 the Wordfence (web application firewall, WAF, for wordpress) team was alerted to a critical vulnerability that was found in essential addons for Elementor that has over 1 million installations. A patch was released for a critical vulnerability that made it possible for any unauthenticated user to reset user passwords including those that have administrative permissions. Rafie Muhammed, security researcher, uncovered this vulnerability and responsibly disclosed it.
It has been observed by the Wordfence team that there have been millions of probing attempts for the read me file of the plugin. This is most likely attackers trying to probe and determine if the plugin is present so they can add it to a list of target sites to exploit. Over 6,900 exploit attempts have already been blocked. The Wordfence team have limited data due to the rule only being triggered if the plugin is installed on ones site and is with a vulnerable version. Unfortunately on the 14th of May 2023, a programmatic exploit was made public on GitHub.
This type of attack gains widespread traction due to the large installation base (over 1 million installations), how easy it is to exploit and the severity of its impact that it can have on WordPress sites. Wordfence threat researchers are expecting that attacks trying to exploit this vulnerability to increase.
Essential Addons for Elementor Vulnerability Details.
- Vulnerability Description: Unauthenticated Arbitrary Password Reset to Privilege Escalation for Essential Addons for Elementor for versions 5.7.1 and lower.
- Affected Plugin: Essential Addons for Elementor
- Affected Versions: Version 5.7.1 and lower
- CVE ID: CVE-2023-32243
- CVSS Score: 9.8 (Critical)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
- Threat Research who uncovered the vulnerability: Rafie Muhammed
- Fully Patched Version: 5.7.2
The patched vulnerability allowed attackers to reset passwords on any of the 1 million WordPress sites that run the affected plugin. this was due to the reset password function not carrying out enough validation for the password reset request with a password reset key. All attackers would need to do is supply a valid user name and obtain a valid nonce from the victim sites home page, in the remaining fields insert random data, and change the supplied user password to what ever the attacker wants.
Usernames are not considered to be sensitive information by WordPress. This means that attackers can enumerate a site hunting for valid usernames. Most of the time site owners either forget to change the default username making it easier for attackers to determine common default usernames such as ‘admin’. This makes it extremely easy for attackers to discover valid accounts that they can then compromise to gain access and to elevate their permissions on the website. Once an attacker has admin access and is logged into the compromised website, they have the ability to perform what ever actions they please, such as installing plugins, backdoors to further compromise the site and server, as well as any visitors to the site.
Attack Data, A Brief Look
Probing to Discover if Plugin is Installed
It is important to note that there are legitimate services which probe for installation data. A trend the Wordfence team observed is that as soon as the vulnerability was disclosed, May 11th 2023, readme.txt probes for the plugin spiked to 5 million probes. This stayed at higher levels than normal over the next few days.
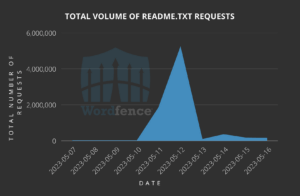
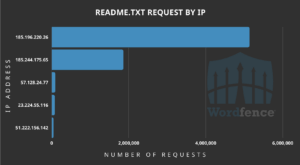
Top IP’s carrying out the discovery probes for readme.txt
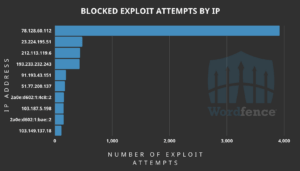
Total number of blocked exploits and the top IP addresses exploiting the vulnerability
Over 6,900 attacks have been blocked by Wordfence. The top attacking IP is 78.128.60.112. Further attacks were blocked trying to exploit the vulnerability a few days after disclosure. If the 6,900 attacks were not blocked by the Wordfence WAF (Web Application Firewall), these attacks would have succeeded in sites being compromised.
IOC (Indicators Of Compromise)
An obvious sign that ones site has been compromised is if the site administrator cannot login with their correct password. This might have been changed through this vulnerability of Essential Addons for Elementor 5.7.1 and older. It is highly recommended to check if any new admin accounts have been added, in order to maintain persistence on ones website.
The Wordfence team are tracking site infections in particular of sites with the vulnerable version and have not yet observed any pattern when it comes to compromising of sites. What was noted that if you are on an outdated version of the plugin those sites were at a much higher risk of infection.
The user agent that is used to carry out this compromise is the following:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36 Edge/16.16299
It is highly recommended as well to check the site’s access logs for the following IP’s:
- 78.128.60.112
- 23.224.195.51
- 212.113.119.6
- 193.233.232.243
- 91.193.43.151
- 51.77.200.137
- 2a0e:d602:1:4c8::2
- 103.187.5.198
- 2a0e:d602:1:bae::2
- 103.149.137.18
To conclude, it is of utmost important to get Essential Addons for Elementor updated to ensure you do not become compromised by this critical vulnerability being exploited. Automatic updates can be enabled for plugins that way one ensures that they are always kept up to date. Some plugins you might run might not have the automatic update feature and those would still need to be updated manually.
Reach out to us on sales@eagleeyet.net if you feel your site has been compromised and to discuss ways to keep ones website safe and secure.
Reference:
Leave a Reply